Observability 101: The Vital Importance of Data in Cybersecurity and how to get it right

Introduction
In today's rapidly evolving digital landscape, cybersecurity stands as the bedrock for safeguarding sensitive information and ensuring the uninterrupted operations of businesses and organizations. As cyber threats continue to advance in sophistication and scale, the reliance on advanced tools and technologies such as Security Information and Event Management (SIEM) and Security Orchestration, Automation, and Response (SOAR) has become non-negotiable. At the heart of these security mechanisms lies the invaluable duo of data and observability, which together form the lifeblood of modern cybersecurity. This blog takes a deep dive into the profound significance of data and observability, shedding light on their critical roles within the Security Operations Center (SOC). Furthermore, we explore how the absence or mishandling of these critical elements can lead to potentially devastating security breaches and vulnerabilities. Lastly, we delve into how Observo.ai's AI-powered observability pipeline comes to the rescue, especially in the context of Cloud, firewall, VPC flow logs, and telemetry data, by addressing these critical challenges.
The Crucial Role of Data and Observability in Cybersecurity
Data and observability are the foundation upon which effective cybersecurity operations are built. They are not merely the conduits of information about potential threats but also the driving force that fuels security mechanisms. To truly appreciate their significance, let's delve deeper into how data and observability play pivotal roles:
- Threat Detection and SIEM: SIEM systems are heavily reliant on a plethora of data and observability inputs, sourced from security event logs, telemetry data, and various other critical sources. This influx of data is channeled into SIEM systems, where it undergoes aggregation and analysis to unveil patterns that may be indicative of security threats.
- SOAR and Incident Response: When a potential security incident arises, data and observability are pivotal in conducting comprehensive investigations. Security analysts lean on historical data to gauge the incident's scope, assess its impact, and decode the tactics, techniques, and procedures (TTPs) employed by malicious actors.
- Enhanced Security Intelligence: In the realm of cybersecurity, professionals utilize data and observability to glean intelligence about emerging threats and vulnerabilities. This invaluable intelligence empowers them to proactively implement security measures, fortify defenses, and safeguard their organization's invaluable assets.
Challenges
While the importance of data and observability is evident, their absence or inadequate handling can seriously compromise an organization's security posture, leading to a litany of issues:
- Incomplete Threat Visibility: A shortage of data and observability sources creates blind spots that could cause security teams to overlook critical events, and indicators of compromise (IoCs), and leave their network vulnerable to undetected threats.
- Sluggish Incident Response: When faced with an insufficiency of data, incident response processes can grind to a halt as security analysts grapple with data shortages, which can severely hamper their ability to effectively assess and mitigate security incidents.
- Ineffective Threat Hunting: Proactive threat hunting, an essential aspect of cybersecurity, is hindered by a lack of historical data. This can make tracking sophisticated threats that may have lurked within the environment for an extended period a monumental challenge.
- Erroneous Decision-Making: Inaccurate, incomplete, or inconsistent data and observability formats can lead to misguided security decisions, including the proliferation of false positives and false negatives. This, in turn, can trigger unnecessary alarms or cause genuine threats to go unnoticed.
Observability Pipelines
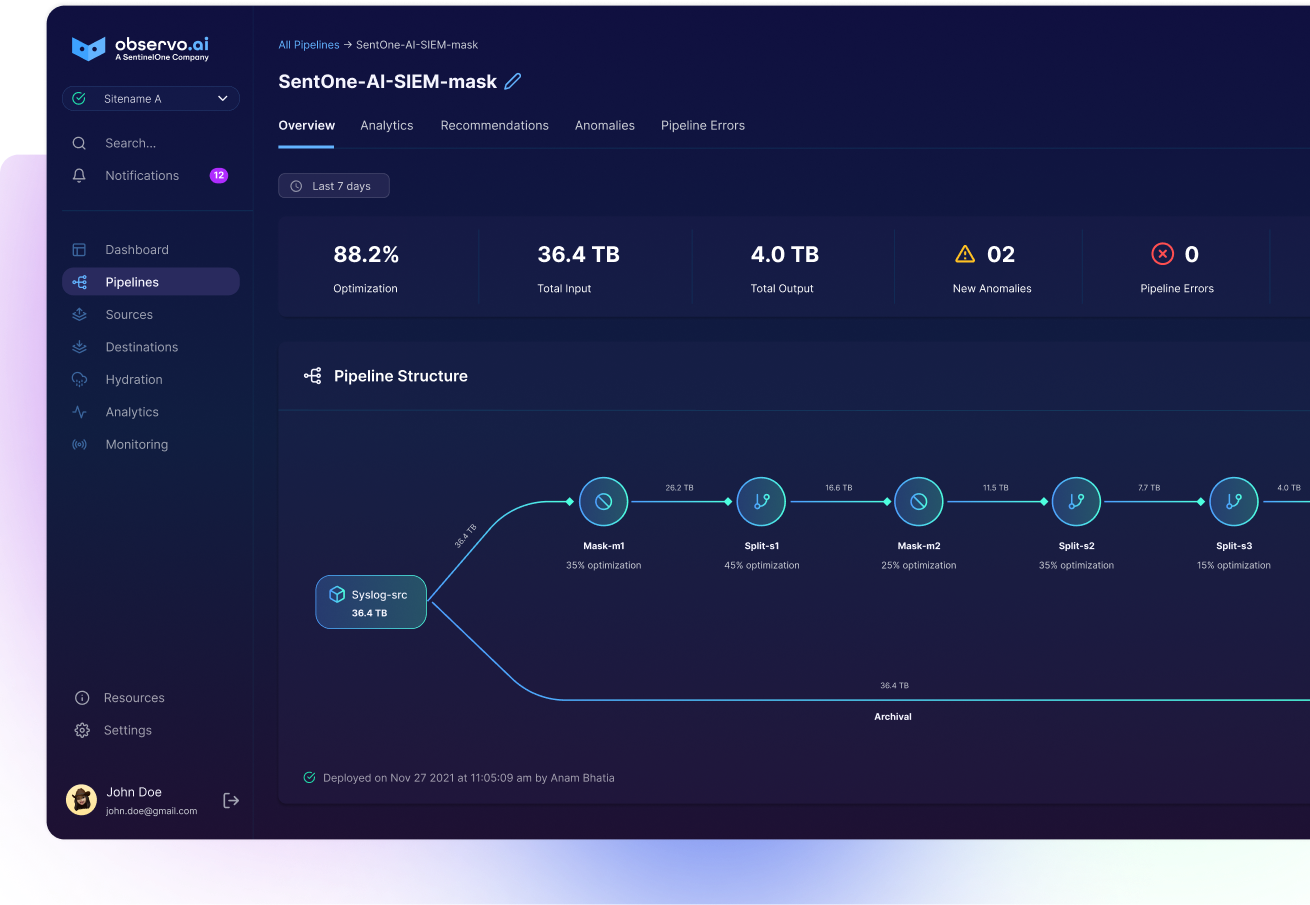
To tackle the challenges posed by data and observability in cybersecurity effectively, Observo.ai steps in with its AI-powered observability pipeline, offering a holistic solution that proficiently addresses these challenges. The platform excels in efficiently routing, optimizing, enriching, and formatting data and observability sources, particularly in the context of Cloud, firewall, VPC flow logs, and telemetry data. Here's how Observo.ai transforms cybersecurity operations:
- Data Routing and Optimization: Observo.ai expertly directs data from a myriad of sources, optimizing data flows to reduce latency. This ensures that security tools, including SIEM and SOAR systems, receive data promptly, resulting in accelerated threat detection and response times.
- Data Enrichment: The platform enriches data with contextual information and additional insights, equipping security analysts with valuable context to expedite incident investigation and streamline decision-making processes.
- Consistent Data Formatting: Observo.ai assures the uniform formatting of data and observability information. This consistency eases the processing and analysis of data by SIEM, SOAR, and other security tools, ultimately reducing false positives and enhancing the precision of threat detection.
Conclusion
Data and observability are the pillars of effective cybersecurity, serving as the backbone for the identification, analysis, and response to threats. The absence or mishandling of data and observability can lead to security breaches and a weakened security posture. Observo.ai's AI-powered observability pipeline offers a comprehensive solution, expertly tackling these challenges and elevating cybersecurity readiness. By harnessing the power of data, observability, and AI-driven technologies, organizations can proactively defend against ever-evolving cyber threats, safeguard their digital assets, and maintain a resilient security posture in the face of an increasingly intricate threat landscape. In the pursuit of robust cybersecurity, data, and observability reign supreme, and Observo.ai is the guiding light illuminating the path forward.